The biggest benefactors of which are Steadfast Solutions clients, who have much peace of mind to gain as a result of this multi-tiered campaign to improve their customer experiences. Two-factor authentication, aka multi-factor authentication, or 2FA, is big right now – primarily due to IT security optimisation being seen globally as paramount in the battle against cybercrime and data breaches.
Over the past twelve months, Steadfast Solutions has been implementing a Continuous Improvement Campaign.
It seeks to bring an optimal level of customer and IT service standards in an aligned and forward-thinking way, such that Melbourne and Brisbane-area business owners concerned about stepping-up their IT support will indeed be able to reach that goal in a short time-frame.
What does this mean for my business?
Steadfast Solutions is striving to improve Melbourne IT service offerings and customer service, to meet the highest possible standards – in security, as with two-factor authentication – and around the IT service spectrum.
It is a process which, in the long term, achieves:
- Greater customer focus;
- Enhanced quality of service delivery; and
- Simplified and fully documented processes and procedures.
How will you achieve optimum customer focus?
We have rolled out a new Learning Management System so that all staff can undergo training on all facets of our business. It allows us to complete administration, documentation, tracking, reporting, e-learning education courses and training programs, online. This will standardise your experience with us, providing a uniform result, regardless of which technician you deal with.
Our Document Management System keeps our documentation in an integrated platform where we can create, track, manage and share. It allows for smarter reuse of documentation, enabling technicians to solve incidents and service requests much more quickly than before. It allows us to get a visual snapshot of your network and where the issues may reside. It assists us to track your licensing and patching requirements so we can keep you up to date with expiring annuities and future roll-outs.
How will you achieve quality of service delivery?
To prove our commitment to service delivery excellence, we have rolled out a Quality Management System throughout all levels of their organisation. This incorporates all aspects of control and assurance measures.
Accordingly, Steadfast’s Melbourne IT staff are measured and audited on:
- Timeliness and Responsiveness;
- Completeness and Accuracy;
- Courtesy; and
- Consistency
This results in levels of efficiency unseen before and value-added service guarantees for you and your business that maximally stretch your dollar!
Over the past year, Steadfast Solutions’ Continuous Customer Service Improvement Campaign has resulted in positive changes like improved IT customer service and customer experience via 2FA data security and much more. Call us at 1300 739 335 or email us at hello@steadfastsolutions.com.au to learn more!
How does your simplifying and fully documenting processes and procedures assist us, as a business?
Through the continuous assessment and enhancement of service offerings, processes, procedures, and attitudes, an environment can be developed where all team members strive for greater levels of quality and customer service.
For instance, recently we have increased our own internal security to help protect our customers’ data.
We are focused on stepping up the use of multi-factor or two-factor authentication (2FA) for our website and help desk portal logins.
And, while we don’t claim to be CIA security experts, with Steadfast Solutions utilising Two Factor Authentication to improve security and further protect our client information — this helps make us a more attractive Melbourne IT company prospect.
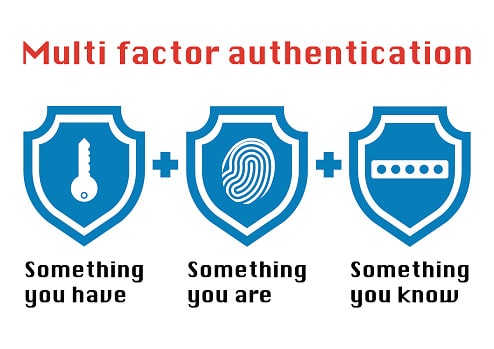
So, what exactly is two-factor authentication, or 2FA?
Two-factor authentication, also called multiple-factor or multiple-step verification, is an authentication mechanism to double check that your identity is legitimate.
Its purpose is to make attackers’ life harder and reduce fraud risks. If you already follow basic password security measures, two-factor authentication will make it more difficult for cybercriminals to breach your account.
Answers to security questions are easy to find out, unfortunately, especially now that we are willingly sharing all the details about our lives on social networks and blogs. Anyone that interacts with us on a daily basis can find out the answers to common security questions, such as the graduation year, the city that you grew up in or our first pet’s name.
Even if you don’t give these out on your Facebook profile, some can be found through public records, available for anyone who cares to look. Others can be cracked simply by entering common names.
This is where two-factor authentication comes in handy. It will offer you an extra layer of protection, besides passwords. It’s hard for cybercriminals to get the second authentication factor; they would have to be much closer to you. This drastically reduces their chances to succeed.
In short, we provide the same stringent levels of data security to our clients as we ourselves utilise.
What will all this cost me as a struggling business owner?
You can get all of our IT services in one affordable package with our managed IT services option. Our flat-rate, monthly fee makes it a much more cost-effective and sensible way to get our customised computer support solutions.
We’re confident we can provide the top-level IT support services Melbourne and Brisbane companies expect and demand. Because let’s face it – anything less would be doing our clients and ourselves a disservice.
We’ve set ourselves apart from other small business IT support companies by making sure each and every one of our clients experiences maximum satisfaction. If they don’t experience it, our job isn’t done right, and we keep working on perfecting our IT customer service and customer experience until you’re glowing with praise.
We’re proud to be among the best IT support companies for small businesses in Melbourne and Brisbane for that and more reasons.
Where do I sign up for your 2FA-enhanced IT services?
If you would like to know more about our two-factor authentication program and how we’re protecting our client data better or for more information on experiencing an enhanced level of customer and IT service, then please contact Steadfast Solutions today at 1300 739 335 or email us at hello@steadfastsolutions.com.au today!